Dynamics 365 CRM has some security features which integrates Dynamics 365 with Active Directory (AD) Groups. AD Groups can be used to grant and restrict access to a Dynamics 365 environment which enhances security as well as simplifies the process of adding users. As is the case with AAD security teams, users get automatically added to the teams as and when they login in to CRM.
In order to create team of type AAD security group in CRM, we need to first create a group in Azure Portal following below steps:
1. Login to the Azure Portal using a Global administrator account for the directory and select Azure Active Directory as shown below.
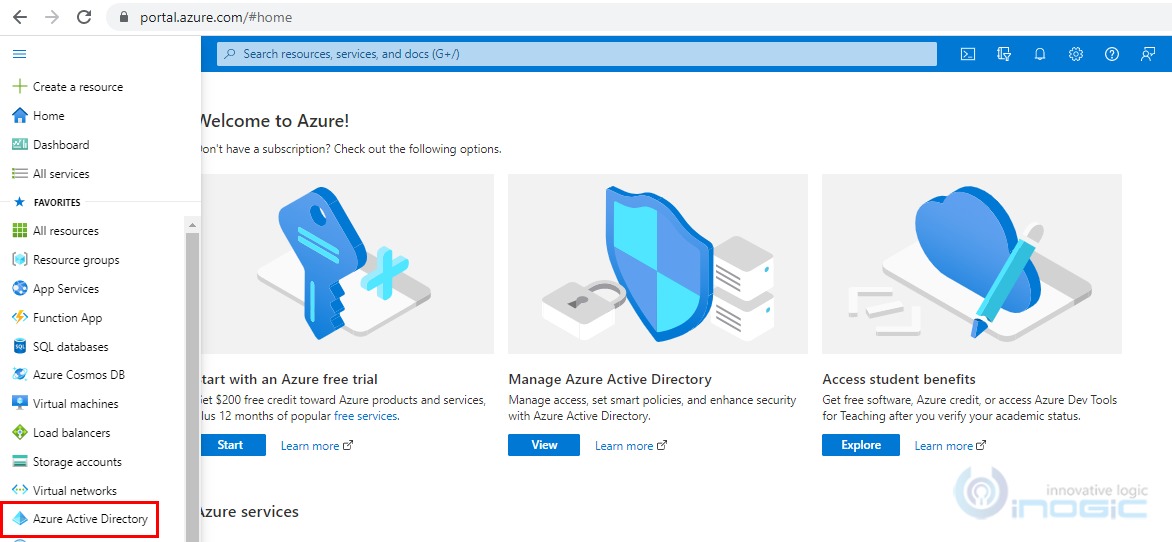
2. On Azure Active Directory Page select Groups.
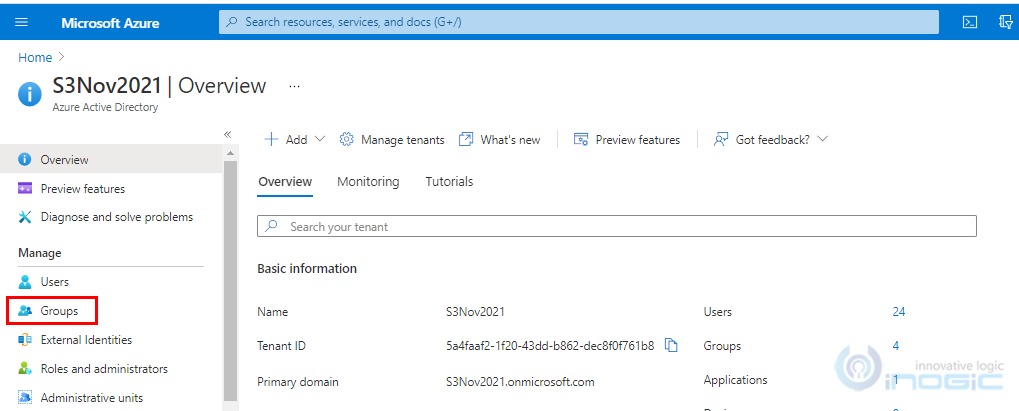
3. Click on New Groups.
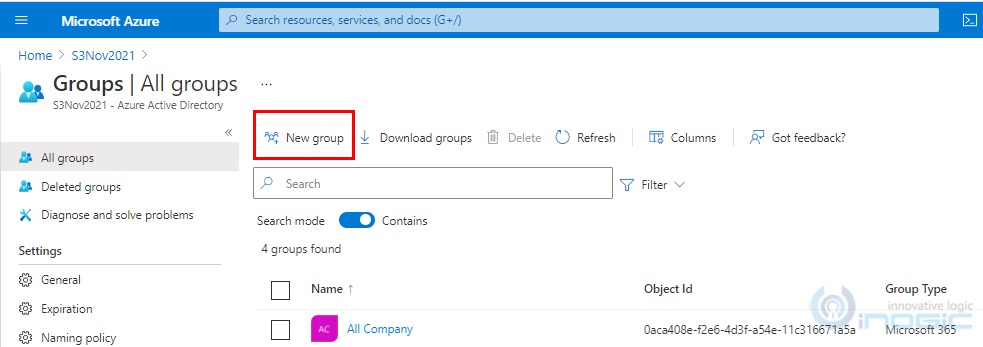
4. New Group pane will appear. Fill in all the required fields and click on create.

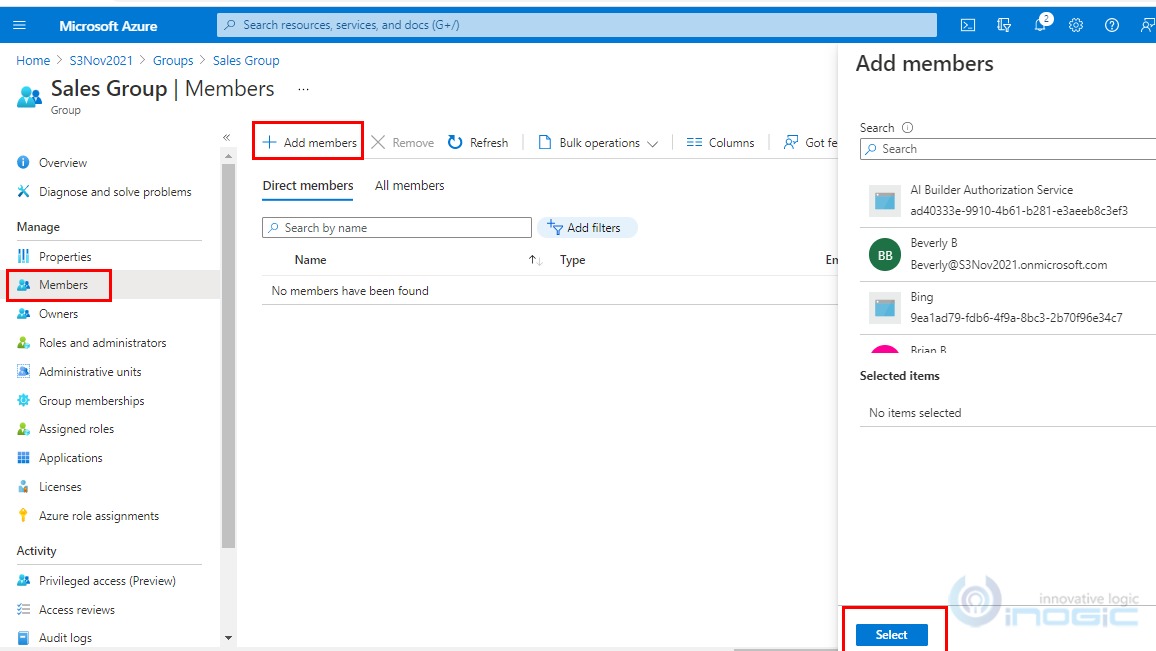
5. Open the Sales Group and then click on
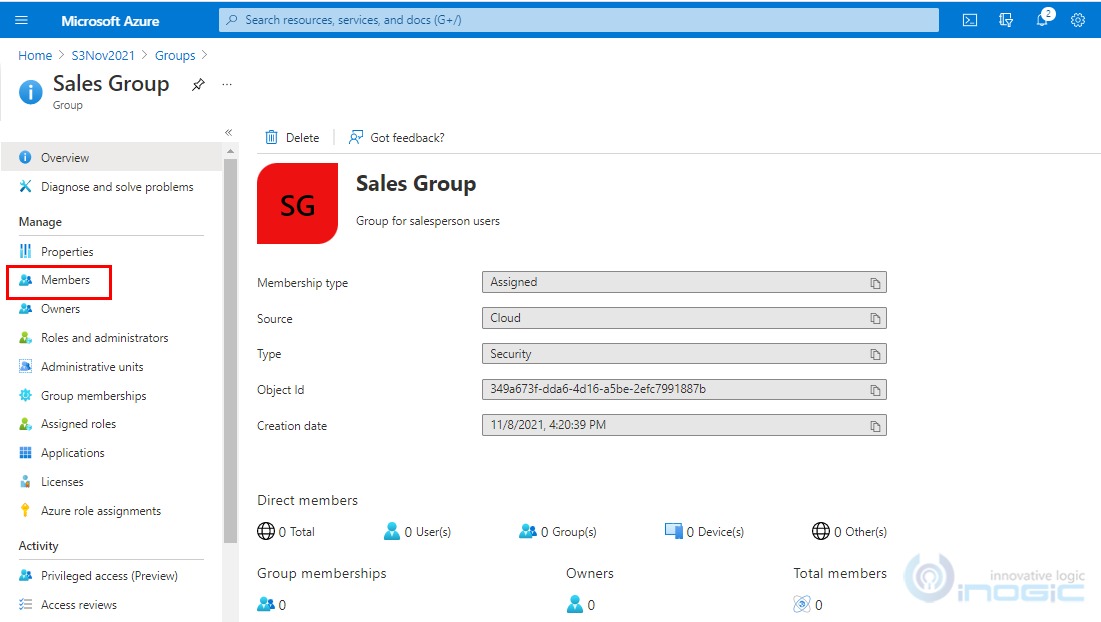
6. Click on Add Members, select the members (License users in CRM having no individual security role) that you want to add in the group and then click on Select button.
7. On click of Group Overview, you will be able to see the number of members added in the group.
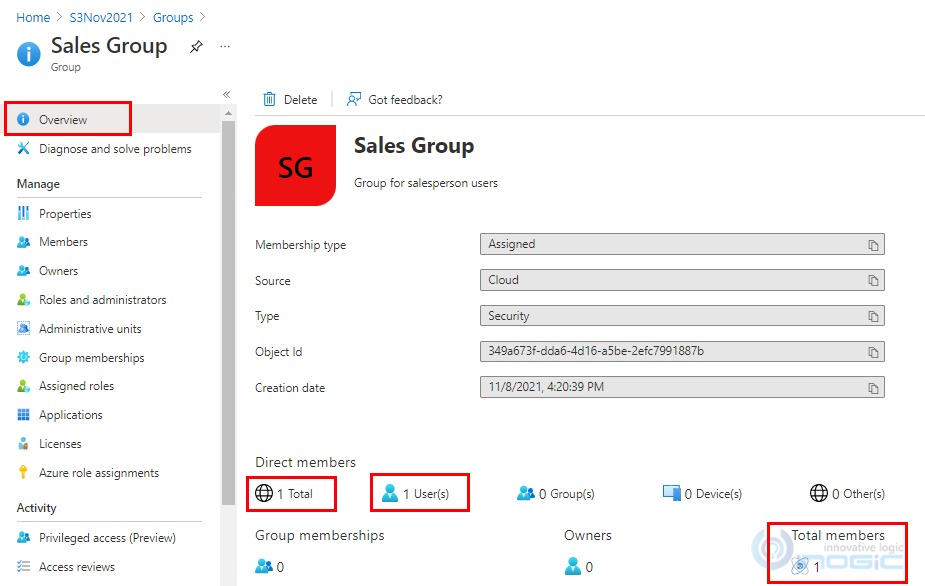
Once the group is created in Azure Portal, we can create team of type AAD Security groups in CRM.
To create Team of type AAD security in CRM follow below steps:
1. Login to the CRM environment as a Global Administrator.
2. Navigate to settings icon and click on Advanced Settings.
3. Under settings select Security.
4. Under security, select Teams.
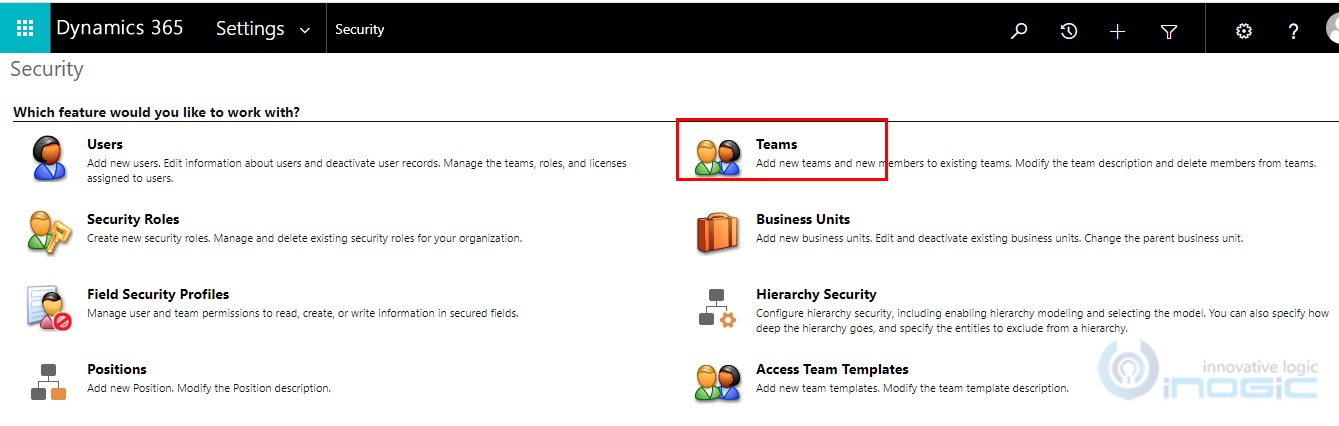
5. Click on +New and enter all the required fields.
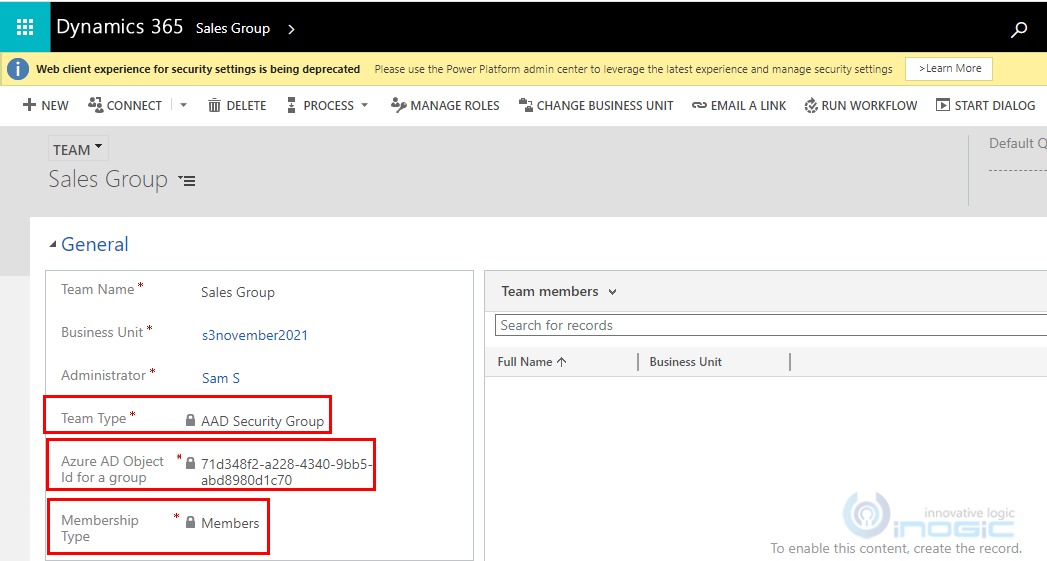
Team Name – Provide valid name for the Team.
Business unit – By default, root business unit is selected. You can select the Business unit as per your business requirement.
Administrator – User having System Administrator rights needs to be selected.
Team Type – Select AAD Security Group.
Azure AD Object Id for a group – This field will be visible on selection of AAD security group in Team Type and the value to enter in this field can be found on the Groups Overview page of Azure Portal.
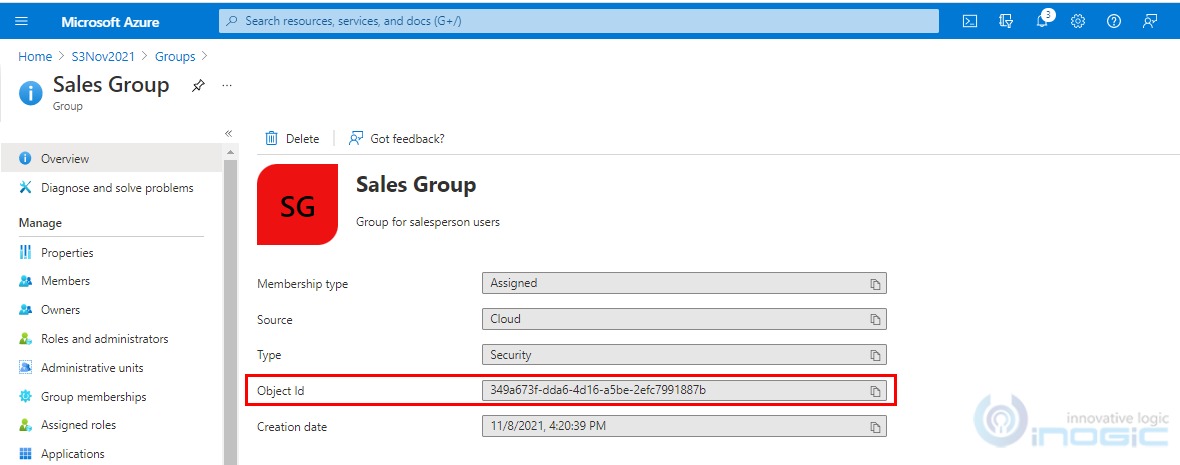
Membership Type – Select the option Members.
Below are the options available for the Membership Type field.
- Members and guests
- Members
- Owners
- Guests
6. Click on Save. Once the Team gets created, assign a security role to the Team by clicking on Manage roles.
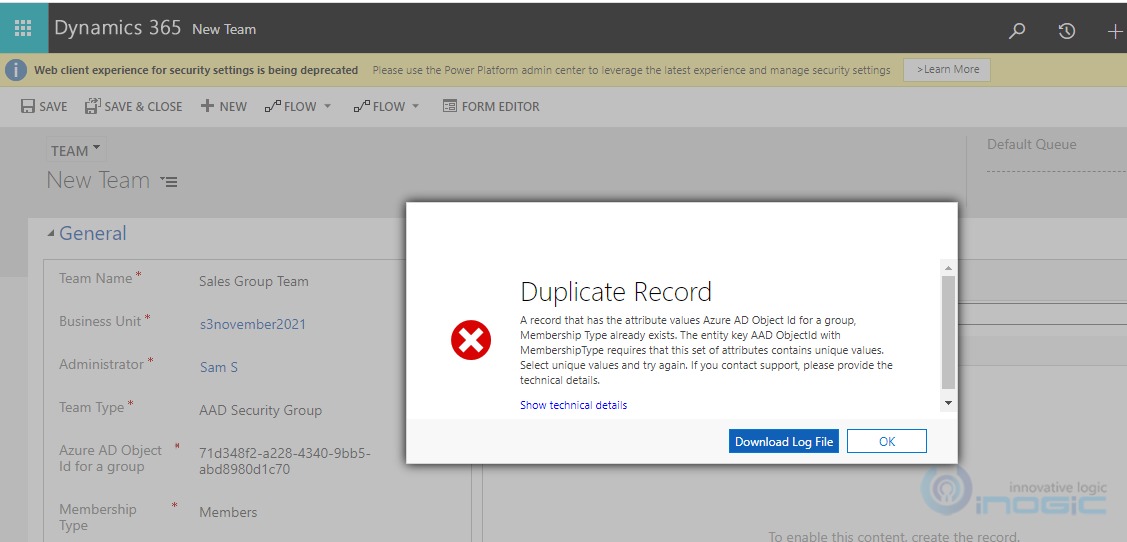
Note: Duplicate Membership Type Teams cannot be created for same Azure AD Object Id.
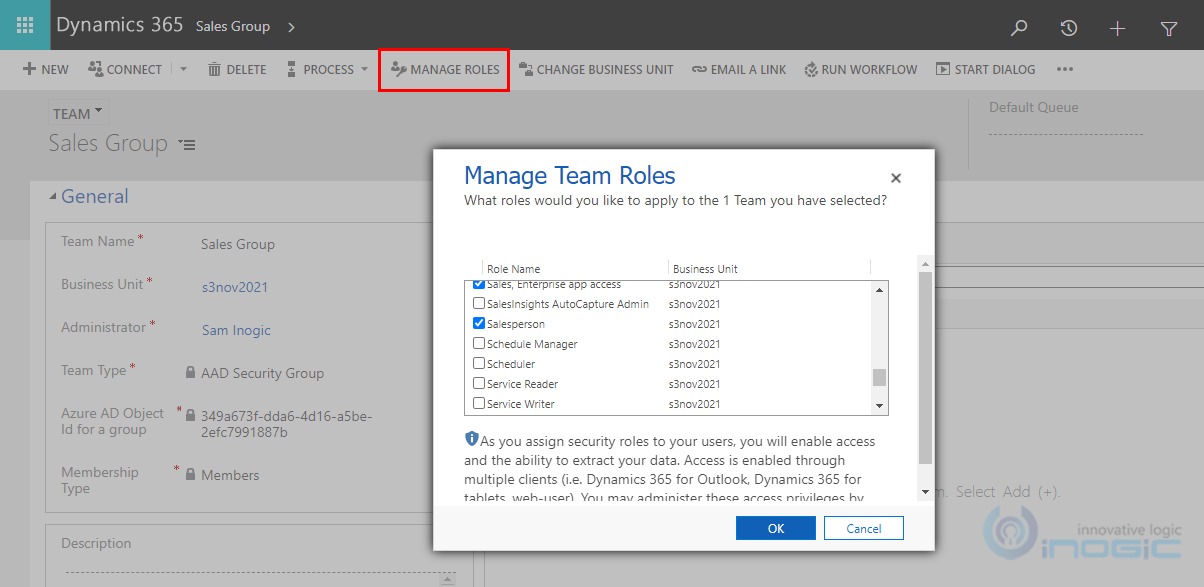
Once a group team is established and created in an environment with a security role, any licensed Dataverse users who are added to the Azure AD group can immediately access the environment.
- Note: The list of team members listed in each group team only displays the user members who have accessed the environment.This list doesn’t show all the group members of the Azure AD group. When an Azure AD group member accesses the environment, the group member is added to the group team. The team member’s privileges are derived dynamically at run-time by inheriting the group team’s security role. Since the security role is assigned to the group team and the group team member inherits the privileges, the security role is not assigned directly to the group team member. Due to the team member’s privileges being derived dynamically at run-time, the team member’s Azure AD group memberships are cached upon the team member’s log-in. This means that any Azure AD group membership maintenance done on the team member in Azure AD will not be reflected until the next time the team member logs in or when the system refreshes the cache (after 8 hours of continuous log-in).
As seen in the above example we selected Members as the Membership Type. Similarly for each Azure AD group, the administrators can create separate group teams with the suitable Membership Type based on the Azure AD group consisting of Members, or Owners, or Guests, or Members and Guests and assign respective security roles to these teams.
Let’s have a look on how to add guest in Azure Portal.
1. Login to Azure Portal as a global administrator.
2. Navigate to left pane and select Azure Active Directory.
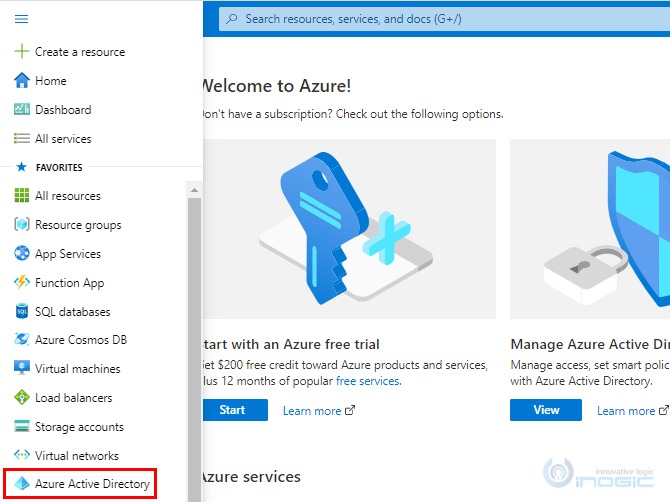
3. Under Manage, select users.

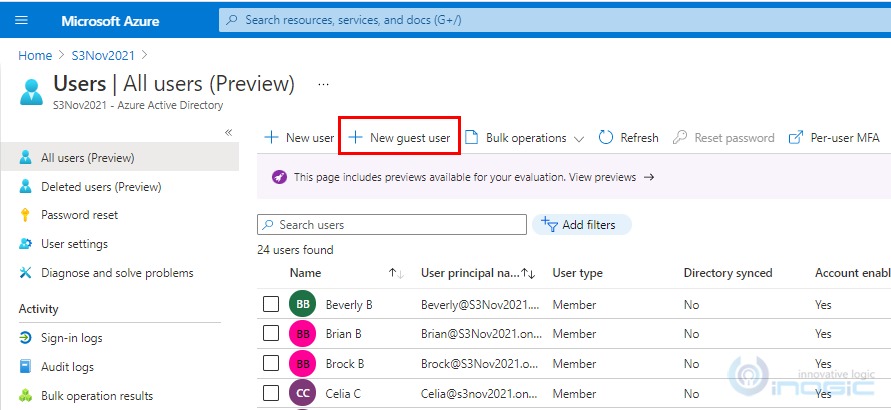
4. Click on +New guest user.
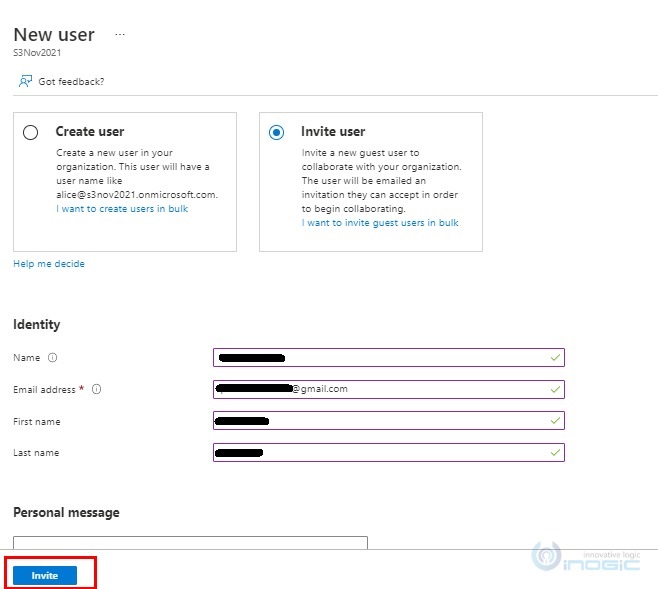
5. By default, Invite user option is selected. Fill in the required details and click on Invite
6. Once the invitation is sent, the guest user gets added in the directory with user type as Guest.
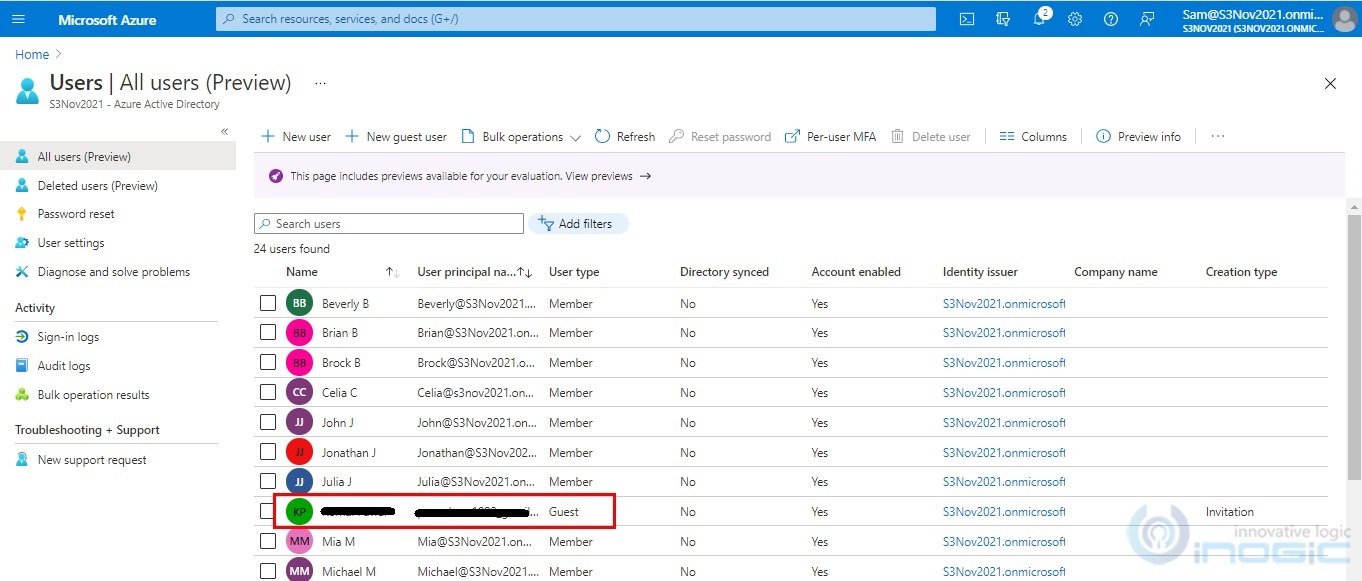
7. The guest user needs to accept the invitation received in their mailbox.
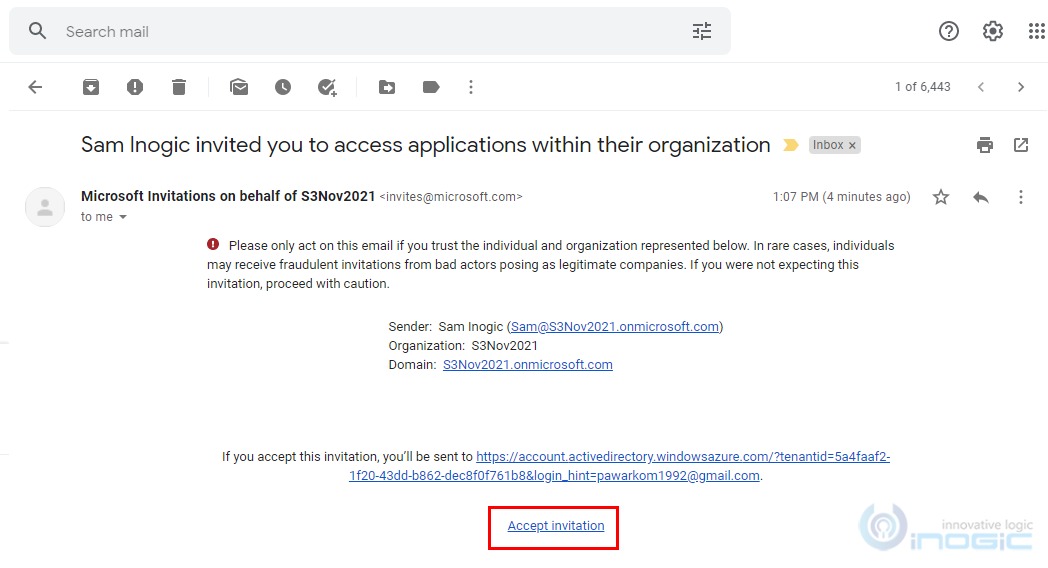
8. Once the invitation is accepted, it will redirect to below page.
The guest user will not get access to the CRM environment unless and until license is assigned to that user. On creation of guest, user license can’t be assigned. To assign the license to the guest user, we need to add the guest user in the group and then assign the license to the group.
9. To assign the license for the guest user already added in the group, navigate to Azure Active Directory >> Groups >> Select the group for which you want to assign the license and then click on Licenses.
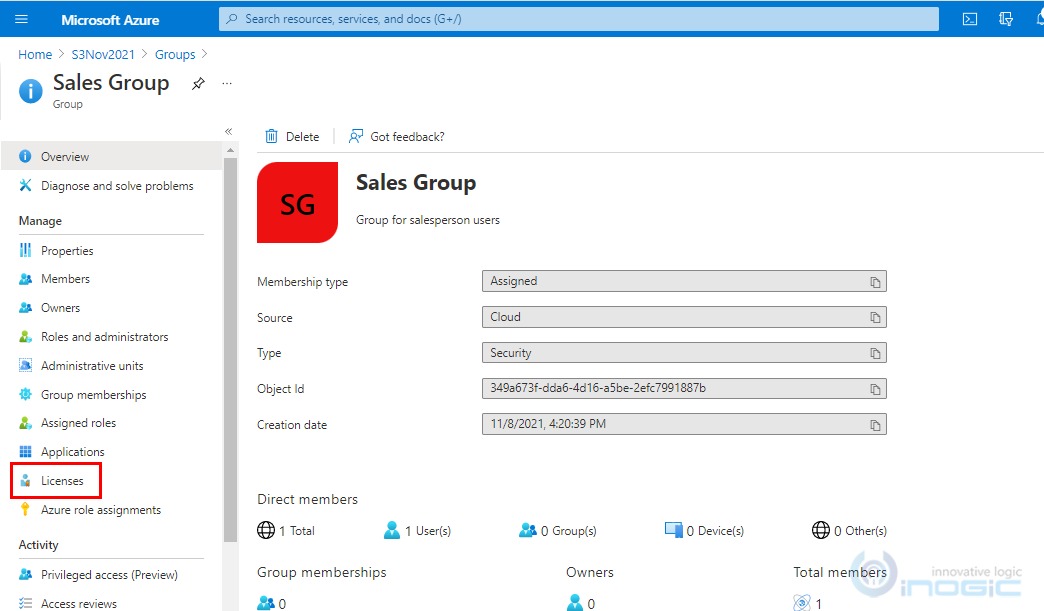
10. Click on + Assignments.
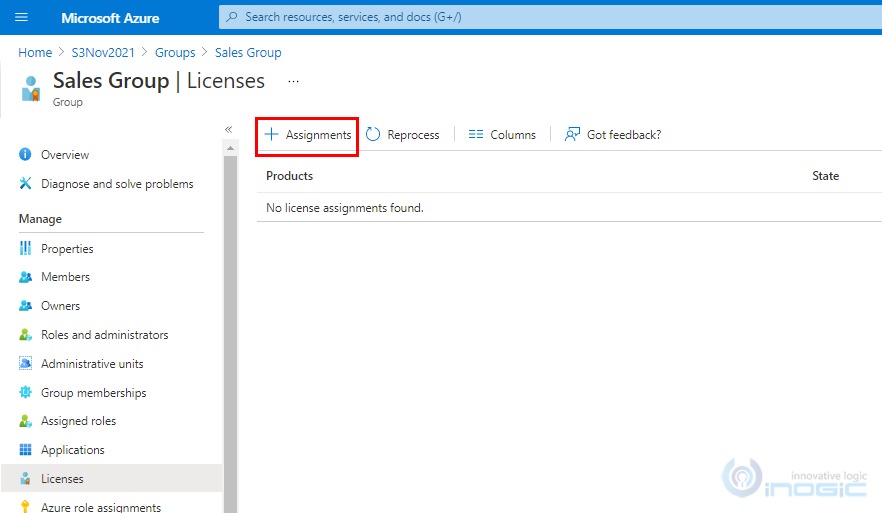
11. Select the appropriate licenses that you need to assign to the group and click on Save.
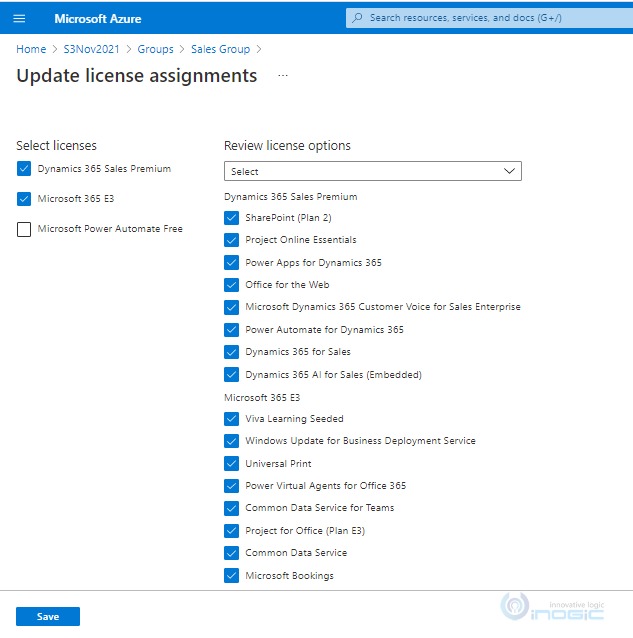
This way we can have guest user added in the Active directory and by creating the Teams of type AAD Security group and keeping the membership type as guest or Member’s and guest in CRM will grant access to those Members and the guest.
Here, though Members, guests and Owners are added in a single group on Azure portal, however their access depends on the Teams along with Membership type created in CRM.
If Membership Type is selected as “Members” even though the guest and owners are present in the group, they will not get access to the CRM environment only Members will get the access.
Similarly, if Membership Type is selected as “Guest” then only guest users will get access and not the Members and the owners.
Conclusion
Thus, AD groups helps to maintain security of the environment by restricting the accidental access of the environment by the users. Also, it provides an easy way of assigning security roles to the users by just providing the security role to AD Teams.

No comments:
Post a Comment